Skynet-Hosting
New member
Since December 2023, various groups have begun using the CLINKSINK drainer to illegally obtain funds and tokens from users of Solana (SOL) cryptocurrency. Drainers, which are malicious scripts and smart contracts, facilitate the unauthorized transfer of funds or digital assets like non-fungible tokens from victims' wallets through deceptive transactions.
These operations have seen the involvement of at least 35 affiliate IDs connected to a drainer-as-a-service (DaaS) framework that employs CLINKSINK. The operators of this DaaS provide these drainer scripts to affiliates, taking approximately 20% of the stolen funds as their share. The estimated total value of assets appropriated in these recent campaigns exceeds $900,000 USD.
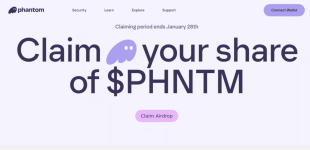
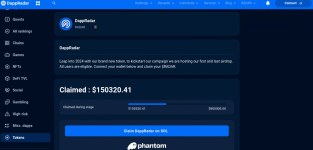
In the recent CLINKSINK Drainer Operations, attackers used social media and chat platforms, including X and Discord, to distribute phishing sites with cryptocurrency themes, aiming to engage victims with the CLINKSINK drainer. These deceptive sites, imitating authentic crypto platforms like Phantom, DappRadar, and BONK, deployed various fake token airdrop baits to initiate the malicious CLINKSINK JavaScript code, leading to wallet connections and subsequent fund theft.
When individuals visit these phishing pages, they are misled into connecting their wallets to receive an alleged token airdrop. After establishing a wallet connection, they are then prompted to approve a transaction, inadvertently giving the drainer service the ability to drain their funds.
Screenshot of $PHNTM airdrop-themed phishing page
Screenshot of DappRadar-themed phishing page
Screenshot of BONK-themed phishing page

Always exercise caution and vigilance when dealing with cryptocurrency transactions. Be skeptical of unsolicited offers, especially those promising free tokens or airdrops. Verify the authenticity of websites and never share your private keys or wallet credentials. Remember, if something seems too good to be true, it probably is. Protecting your digital assets is paramount in the ever-evolving landscape of online security.
These operations have seen the involvement of at least 35 affiliate IDs connected to a drainer-as-a-service (DaaS) framework that employs CLINKSINK. The operators of this DaaS provide these drainer scripts to affiliates, taking approximately 20% of the stolen funds as their share. The estimated total value of assets appropriated in these recent campaigns exceeds $900,000 USD.
In the recent CLINKSINK Drainer Operations, attackers used social media and chat platforms, including X and Discord, to distribute phishing sites with cryptocurrency themes, aiming to engage victims with the CLINKSINK drainer. These deceptive sites, imitating authentic crypto platforms like Phantom, DappRadar, and BONK, deployed various fake token airdrop baits to initiate the malicious CLINKSINK JavaScript code, leading to wallet connections and subsequent fund theft.
When individuals visit these phishing pages, they are misled into connecting their wallets to receive an alleged token airdrop. After establishing a wallet connection, they are then prompted to approve a transaction, inadvertently giving the drainer service the ability to drain their funds.
Screenshot of $PHNTM airdrop-themed phishing page

Screenshot of DappRadar-themed phishing page

Screenshot of BONK-themed phishing page

Always exercise caution and vigilance when dealing with cryptocurrency transactions. Be skeptical of unsolicited offers, especially those promising free tokens or airdrops. Verify the authenticity of websites and never share your private keys or wallet credentials. Remember, if something seems too good to be true, it probably is. Protecting your digital assets is paramount in the ever-evolving landscape of online security.